What Is Cloud Container Security . container security is the practice of implementing mechanisms/processes to secure containerized applications and. It involves defining and adhering to. container security refers to the tools and processes that help protect container applications by detecting and mitigating. These tools detect vulnerabilities and threats in container workloads and the underlying platforms. container security is the process of safeguarding containerized applications from malware and other vulnerabilities. container security involves protecting containerized applications and their infrastructure throughout their lifecycle, from development to.
from docs.microsoft.com
These tools detect vulnerabilities and threats in container workloads and the underlying platforms. container security refers to the tools and processes that help protect container applications by detecting and mitigating. It involves defining and adhering to. container security involves protecting containerized applications and their infrastructure throughout their lifecycle, from development to. container security is the practice of implementing mechanisms/processes to secure containerized applications and. container security is the process of safeguarding containerized applications from malware and other vulnerabilities.
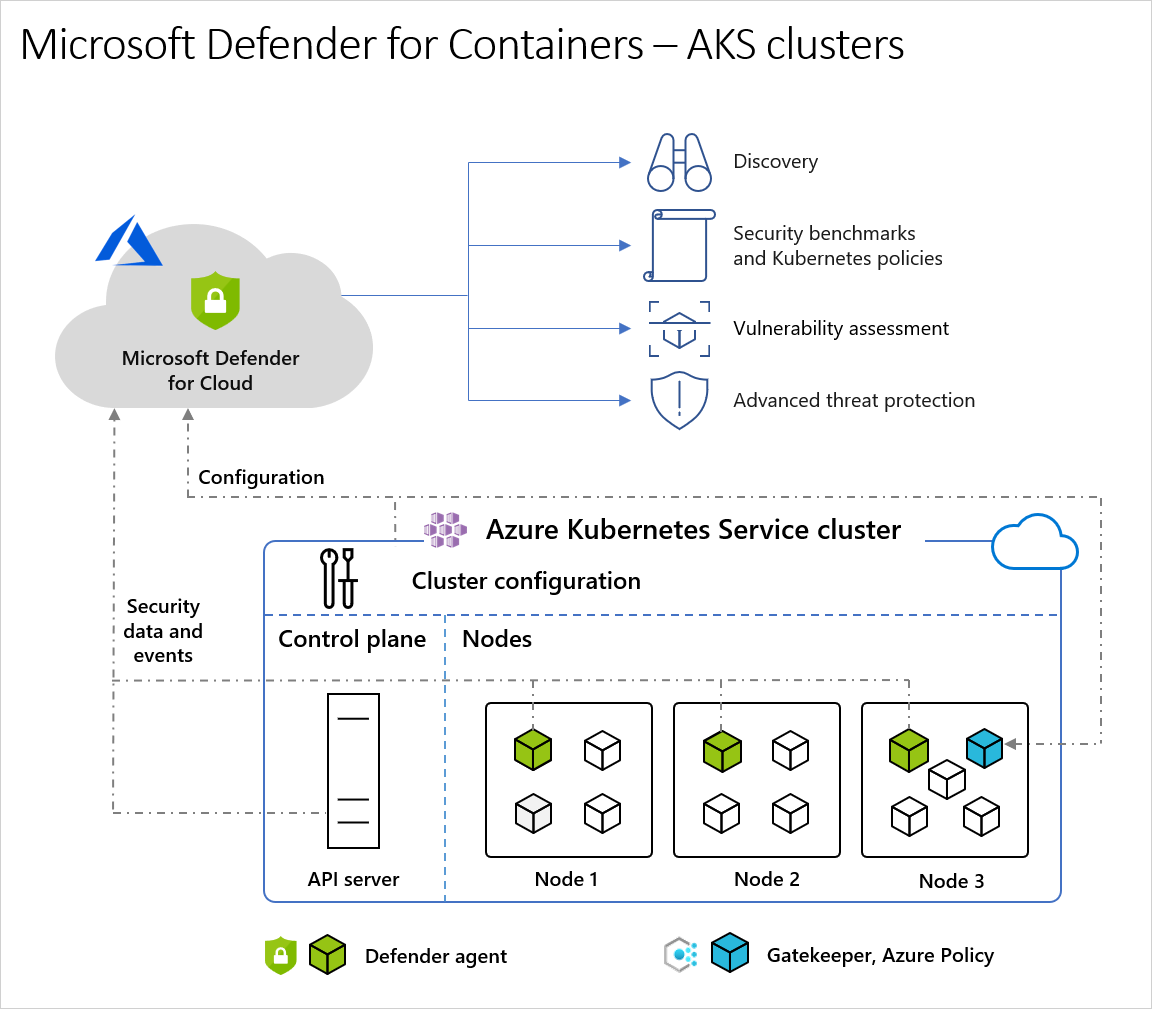
Container security architecture in Microsoft Defender for Cloud
What Is Cloud Container Security These tools detect vulnerabilities and threats in container workloads and the underlying platforms. container security refers to the tools and processes that help protect container applications by detecting and mitigating. container security is the practice of implementing mechanisms/processes to secure containerized applications and. It involves defining and adhering to. container security is the process of safeguarding containerized applications from malware and other vulnerabilities. container security involves protecting containerized applications and their infrastructure throughout their lifecycle, from development to. These tools detect vulnerabilities and threats in container workloads and the underlying platforms.
From library.devops.com
Best Practices for Cloud and Container Security What Is Cloud Container Security container security involves protecting containerized applications and their infrastructure throughout their lifecycle, from development to. container security refers to the tools and processes that help protect container applications by detecting and mitigating. container security is the process of safeguarding containerized applications from malware and other vulnerabilities. It involves defining and adhering to. These tools detect vulnerabilities and. What Is Cloud Container Security.
From www.ipoque.com
Container security in the cloud How network visibility helps ipoque What Is Cloud Container Security These tools detect vulnerabilities and threats in container workloads and the underlying platforms. container security refers to the tools and processes that help protect container applications by detecting and mitigating. container security is the practice of implementing mechanisms/processes to secure containerized applications and. container security is the process of safeguarding containerized applications from malware and other vulnerabilities.. What Is Cloud Container Security.
From www.provision.ro
ProVision Cloud Security Container Security What Is Cloud Container Security These tools detect vulnerabilities and threats in container workloads and the underlying platforms. It involves defining and adhering to. container security is the process of safeguarding containerized applications from malware and other vulnerabilities. container security refers to the tools and processes that help protect container applications by detecting and mitigating. container security involves protecting containerized applications and. What Is Cloud Container Security.
From docs.microsoft.com
Container security architecture in Microsoft Defender for Cloud What Is Cloud Container Security These tools detect vulnerabilities and threats in container workloads and the underlying platforms. container security is the process of safeguarding containerized applications from malware and other vulnerabilities. container security refers to the tools and processes that help protect container applications by detecting and mitigating. It involves defining and adhering to. container security is the practice of implementing. What Is Cloud Container Security.
From www.iansresearch.com
Top 10 Container Security Tools for the Cloud IANS Research What Is Cloud Container Security container security is the process of safeguarding containerized applications from malware and other vulnerabilities. It involves defining and adhering to. container security refers to the tools and processes that help protect container applications by detecting and mitigating. container security is the practice of implementing mechanisms/processes to secure containerized applications and. container security involves protecting containerized applications. What Is Cloud Container Security.
From carbonblack.vmware.com
Carbon Black Cloud Container Security Technical Overview VMware What Is Cloud Container Security container security is the practice of implementing mechanisms/processes to secure containerized applications and. container security refers to the tools and processes that help protect container applications by detecting and mitigating. container security involves protecting containerized applications and their infrastructure throughout their lifecycle, from development to. These tools detect vulnerabilities and threats in container workloads and the underlying. What Is Cloud Container Security.
From blog.devops.dev
Security Context — Capabilities explained. by Sagar What Is Cloud Container Security container security is the process of safeguarding containerized applications from malware and other vulnerabilities. It involves defining and adhering to. container security refers to the tools and processes that help protect container applications by detecting and mitigating. container security involves protecting containerized applications and their infrastructure throughout their lifecycle, from development to. These tools detect vulnerabilities and. What Is Cloud Container Security.
From carbonblack.vmware.com
Carbon Black Cloud Container Security Technical Overview VMware What Is Cloud Container Security It involves defining and adhering to. container security refers to the tools and processes that help protect container applications by detecting and mitigating. These tools detect vulnerabilities and threats in container workloads and the underlying platforms. container security is the practice of implementing mechanisms/processes to secure containerized applications and. container security involves protecting containerized applications and their. What Is Cloud Container Security.
From techcrunch.com
Securing Virtual ContainerBased Applications TechCrunch What Is Cloud Container Security container security involves protecting containerized applications and their infrastructure throughout their lifecycle, from development to. These tools detect vulnerabilities and threats in container workloads and the underlying platforms. container security refers to the tools and processes that help protect container applications by detecting and mitigating. container security is the practice of implementing mechanisms/processes to secure containerized applications. What Is Cloud Container Security.
From blog.qualys.com
Securing your Cloud and Container DevOps Pipeline Qualys Blog What Is Cloud Container Security container security is the process of safeguarding containerized applications from malware and other vulnerabilities. It involves defining and adhering to. container security refers to the tools and processes that help protect container applications by detecting and mitigating. container security involves protecting containerized applications and their infrastructure throughout their lifecycle, from development to. These tools detect vulnerabilities and. What Is Cloud Container Security.
From www.eescorporation.com
Cloud security A Detailed guide EES Corporation What Is Cloud Container Security container security is the process of safeguarding containerized applications from malware and other vulnerabilities. container security involves protecting containerized applications and their infrastructure throughout their lifecycle, from development to. container security refers to the tools and processes that help protect container applications by detecting and mitigating. It involves defining and adhering to. These tools detect vulnerabilities and. What Is Cloud Container Security.
From prophaze.com
Why Is Container Security Important? What Are The Top 10 Docker What Is Cloud Container Security container security involves protecting containerized applications and their infrastructure throughout their lifecycle, from development to. It involves defining and adhering to. container security is the process of safeguarding containerized applications from malware and other vulnerabilities. These tools detect vulnerabilities and threats in container workloads and the underlying platforms. container security refers to the tools and processes that. What Is Cloud Container Security.
From www.dailyhostnews.com
McAfee Cloud Workload Security with container support to aid What Is Cloud Container Security These tools detect vulnerabilities and threats in container workloads and the underlying platforms. container security refers to the tools and processes that help protect container applications by detecting and mitigating. container security involves protecting containerized applications and their infrastructure throughout their lifecycle, from development to. container security is the process of safeguarding containerized applications from malware and. What Is Cloud Container Security.
From ca-security.inforisktoday.com
Securing Container and Cloud Native Applications An Illustrated Guide What Is Cloud Container Security container security refers to the tools and processes that help protect container applications by detecting and mitigating. container security involves protecting containerized applications and their infrastructure throughout their lifecycle, from development to. These tools detect vulnerabilities and threats in container workloads and the underlying platforms. container security is the process of safeguarding containerized applications from malware and. What Is Cloud Container Security.
From www.synopsys.com
What is Cloudnative Container Security? Synopsys What Is Cloud Container Security It involves defining and adhering to. container security refers to the tools and processes that help protect container applications by detecting and mitigating. container security is the process of safeguarding containerized applications from malware and other vulnerabilities. container security is the practice of implementing mechanisms/processes to secure containerized applications and. These tools detect vulnerabilities and threats in. What Is Cloud Container Security.
From www.paloaltonetworks.co.uk
Prisma Cloud Container Security with GKE Autopilot Palo Alto Networks What Is Cloud Container Security container security refers to the tools and processes that help protect container applications by detecting and mitigating. container security is the practice of implementing mechanisms/processes to secure containerized applications and. These tools detect vulnerabilities and threats in container workloads and the underlying platforms. It involves defining and adhering to. container security involves protecting containerized applications and their. What Is Cloud Container Security.
From gogetsecure.com
Why Cloud Security is Important [+5 Benefits You Don't Want to Miss] What Is Cloud Container Security container security refers to the tools and processes that help protect container applications by detecting and mitigating. These tools detect vulnerabilities and threats in container workloads and the underlying platforms. container security is the process of safeguarding containerized applications from malware and other vulnerabilities. container security is the practice of implementing mechanisms/processes to secure containerized applications and.. What Is Cloud Container Security.
From globalcloudplatforms.com
Monitor And Secure Your Containers With New Container Threat Detection What Is Cloud Container Security It involves defining and adhering to. These tools detect vulnerabilities and threats in container workloads and the underlying platforms. container security is the practice of implementing mechanisms/processes to secure containerized applications and. container security refers to the tools and processes that help protect container applications by detecting and mitigating. container security involves protecting containerized applications and their. What Is Cloud Container Security.